ACTIVE sets up a decoy machine on the Internet— ,in also known as a honeypot—which is intentionally infected by malware through vulnerability set in advance. Generally, parties sending malware are recognized to have malware infection. ACTIVE tries to identity the parties in cooperation with ISPs and these ISPs warn the parties to take appropriate countermeasures to remove malware.
The illustration below outlines the flow for this action
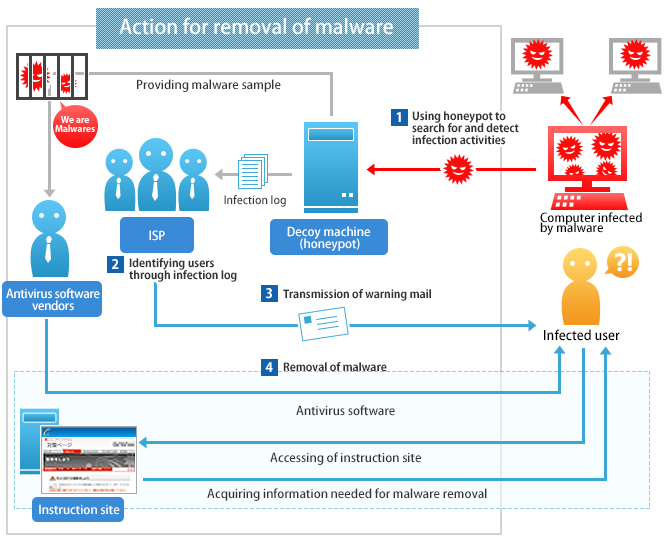
ACTIVE sets up decoy machines, or honeypots, on the Internet and begins malware captures.
Using the malware collected by the honeypots, the ISPs are provided with information on when and from where the malware came, in order to identify which users are likely to have malware infection.
The ISPs send warning mails to users who are reconized to have malware infection, with the URL of the instruction site .
The Internet users access the instruction site and get information needed to remove malware.
The instruction site provides useful information such as antivirus vendors' site where antivirus softwares can be downloaded to remove malware.