In recent years, the most frequent malware infection route is through malware-embedded sites. Some of these sites are counterfeits of famous websites, or tampered ones. These sites are difficult for Internet users to distinguish, and therefore users may not be aware that they have malware infection.
This is why ACTIVE was launched. In the ACTIVE project, decoy machines, or patrolling honeypots, access many different websites to confirm malware-embedded websites create a list of these sites. Referring to the list, ISPs send warning statement to users who agreed in advance that they may have warning statements when they are accessing malware-embedded websites.
Also, ACTIVE tries to contact the administrators of these sites to request removal of malware from their sites.
The illustration below outlines the flow for this action.
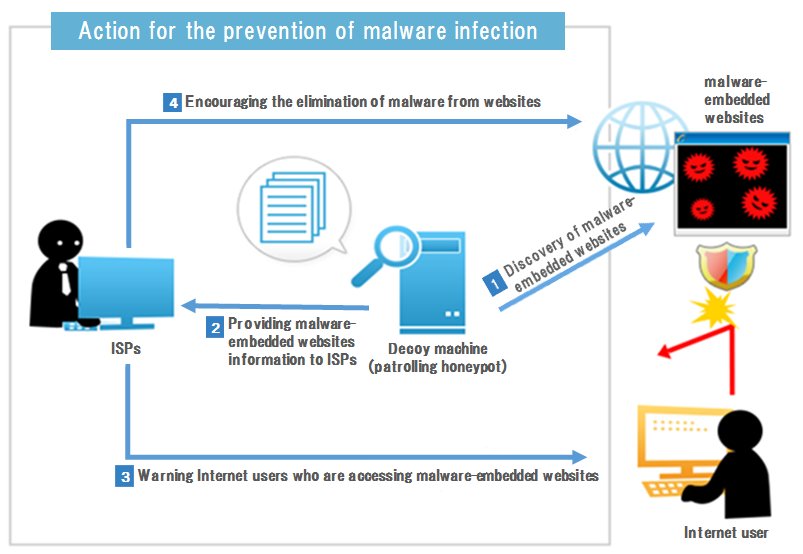
A decoy machine -the patrolling honeypot- is connected to the Internet. The machine accesses a number of websites every day, collecting information on any malware-embedded websites to be listed.
Information on malware-embedded websites is provided to ISPs. As of November 2013, the following services have put in place for prevention of malware infection:
Nifty Corporation Security 24 (Nifty)
Net Barrier Basic (NTT Plala)
Having received prior consent, ISPs send warning statements to Internet users when they are accessing malware-embedded websites.
ISPs send warning statements to the administrators of websites discovered to have embedded malware to request removal of malware from their sites.